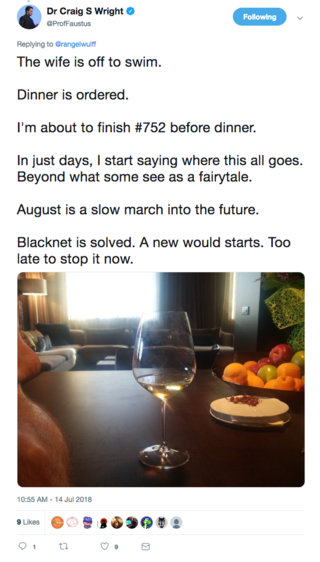
Oh my Satoshi
BlackNet
<h3>BlackNet solved!</h3>
14th July 2018
BlackNet ?
Paper 758
posted by Craig S Wright on 16 Jul 2018
Source:
https://twitter.com
![<h2>Tim May, Father of 'Crypto Anarchy,' Is Dead at 66</h2>
<p>Jim Epstein</p>
<p><strong>The Cypherpunk co-founder was a major influence on both bitcoin and WikiLeaks.</strong></p>
<p>Tim May, co-founder of the influential Cypherpunks mailing list and a significant influence on both bitcoin and WikiLeaks, passed away last week at his home in Corralitos, California. The news was announced Saturday on a Facebook post written by his friend Lucky Green.</p>
<p>In his influential 1988 essay, "The Crypto Anarchist Manifesto," May predicted that advances in computer technology would eventually allow "individuals and groups to communicate and interact with each other" anonymously and without government intrusion. "These developments will alter completely the nature of government regulation [and] the ability to tax and control economic interactions," he wrote.</p>
<p>A deeply private person, May's aversion to outside intrusions defined his philosophical outlook. "'Leave me alone,'" he wrote, is "at the root of libertarianism more so than formal theories about the nature of man."</p>
<p>"My political philosophy is keep your hands off my stuff….Out of my files, out of my office, off what I eat, drink, and smoke," he once told journalist Andy Greenberg.</p>
<p><a href="https://reason.com/2018/12/16/tim-may-influential-writer-on-crypto-ana/" target="_blank">Read on</a></p>
<p>Published by reason.com on 12.16.2018</p>
<p>Source: <a href="https://reason.com/2018/12/16/tim-may-influential-writer-on-crypto-ana/" target="_blank">reason.com</a></p>
<p> </p>](/system/files/611d04/54342b82509200174c/w_medium_Screenshot_2021-08-18_at_14.59.29.png)
Craig Wright talks about Timothy May
(Starting from 2:39)
JD: How did you get into the whole Bitcoin world? You were presumably very very early on in the game.
CW: I've been involved in the whole Bitcoin world the whole time. I’ve been involved in the nature of security and crypto currencies since the the 90s. I was sort of … I met Tim May back in the early 90s and although we have some very different ideas of sort of philosophy of all this, we have some overlaps and parallels as well, so Tim would have been a lot more like you, I guess, the crypto anarchist where I'm the terrible business economist type, companies-are-a-good person and small government but allow companies to get on with it.
Published by The James Delingpole Channel on 18.10.2018
Source:
https://youtu.be/Yr3aiicJq8I
One experimental "information market" is BlackNet, a system which appeared in 1993 and which allows fully-anonymous, two-way exchanges of information of all sorts. There are reports that U.S. authorities have investigated this because of its presence on networks at Defense Department research labs. Not much they can do about it, of course, and more such entities are expected.
Source:
Crypto Anarchy and Virtual Communities
published by Timothy C. May
December 1994
http://groups.csail.mit.edu
JW Weatherman Interviews Cypherpunk Legend Timothy C May—Author of the Cyphernomicon
Published by JW Weatherman on 09.06.2018
Source:
https://www.youtube.com/watch?v=MrGLraSiRZk
‘Back in 1997 there was Tim May’s BlackNet …’ May was a crypto-anarchist, who had been operating and agitating in the cypherpunk community since the mid-1980s. ‘Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner,’ he wrote in the Crypto-Anarchist Manifesto in 1988. BlackNet operated like a precursor to WikiLeaks, soliciting secret information with payments made by untraceable, digital money.
‘We all have a narcissistic hubris,’ Wright told me. He wanted to take May’s BlackNet idea further.
quoted from:
The Satoshi Affair by Andrew O’Haganhttps://www.lrb.co.uk/v38/n13/andrew-ohagan/the-satoshi-affair
Bitcoin’s Smart Future: Artificial Intelligence, Intelligent Bots & How The Bitcoin Network Will Change the World
“How can any government stop that?”
Wright asked rhetorically.
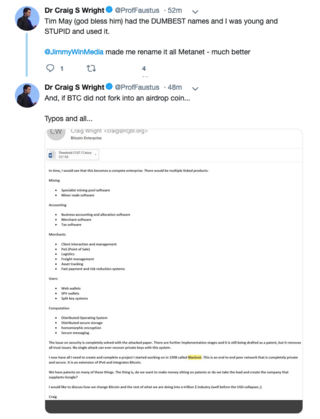
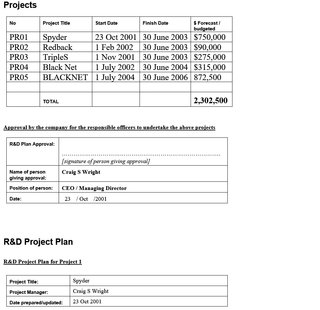
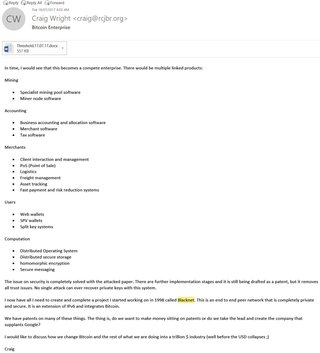
Bitcoin, so often seen as ‘merely’ a payment mechanism, would enable all these amazing transformations by being a highly efficient, connected and secure network. Wright explained that one of his projects back in the late 1990s was called Blacknet. The name was not meant to be understood in the same way as ‘dark web’ or ’dark net’ is today, but rather because it “was dark, as in 100% private”, and users would be in complete control.
Craig Wright at iGaming Super Show July 13, 2017 Amsterdam
Source1:
http://www.igamingbusiness.com
Source2:
https://www.youtube.com
bmoney
Published in 2006(?) by wei dai
I am fascinated by Tim May's crypto-anarchy. Unlike the communities traditionally associated with the word "anarchy", in a crypto-anarchy the government is not temporarily destroyed but permanently forbidden and permanently unnecessary. It's a community where the threat of violence is impotent because violence is impossible, and violence is impossible because its participants cannot be linked to their true names or physical locations.
Until now it's not clear, even theoretically, how such a community could operate. A community is defined by the cooperation of its participants, and efficient cooperation requires a medium of exchange (money) and a way to enforce contracts. Traditionally these services have been provided by the government or government sponsored institutions and only to legal entities. In this article I describe a protocol by which these services can be provided to and by untraceable entities.
I will actually describe two protocols. The first one is impractical, because it makes heavy use of a synchronous and unjammable anonymous broadcast channel. However it will motivate the second, more practical protocol. In both cases I will assume the existence of an untraceable network, where senders and receivers are identified only by digital pseudonyms (i.e. public keys) and every messages is signed by its sender and encrypted to its receiver.
In the first protocol, every participant maintains a (seperate) database of how much money belongs to each pseudonym. These accounts collectively define the ownership of money, and how these accounts are updated is the subject of this protocol.
-
The creation of money. Anyone can create money by broadcasting the solution to a previously unsolved computational problem. The only conditions are that it must be easy to determine how much computing effort it took to solve the problem and the solution must otherwise have no value, either practical or intellectual. The number of monetary units created is equal to the cost of the computing effort in terms of a standard basket of commodities. For example if a problem takes 100 hours to solve on the computer that solves it most economically, and it takes 3 standard baskets to purchase 100 hours of computing time on that computer on the open market, then upon the broadcast of the solution to that problem everyone credits the broadcaster's account by 3 units.
-
The transfer of money. If Alice (owner of pseudonym KA) wishes to transfer X units of money to Bob (owner of pseudonym KB), she broadcasts the message "I give X units of money to KB" signed by KA. Upon the broadcast of this message, everyone debits KA's account by X units and credits KB's account by X units, unless this would create a negative balance in K_A's account in which case the message is ignored.
-
The effecting of contracts. A valid contract must include a maximum reparation in case of default for each participant party to it. It should also include a party who will perform arbitration should there be a dispute. All parties to a contract including the arbitrator must broadcast their signatures of it before it becomes effective. Upon the broadcast of the contract and all signatures, every participant debits the account of each party by the amount of his maximum reparation and credits a special account identified by a secure hash of the contract by the sum the maximum reparations. The contract becomes effective if the debits succeed for every party without producing a negative balance, otherwise the contract is ignored and the accounts are rolled back. A sample contract might look like this:
KA agrees to send KB the solution to problem P before 0:0:0 1/1/2000. KB agrees to pay KA 100 MU (monetary units) before 0:0:0 1/1/2000. KC agrees to perform arbitration in case of dispute. KA agrees to pay a maximum of 1000 MU in case of default. KB agrees to pay a maximum of 200 MU in case of default. KC agrees to pay a maximum of 500 MU in case of default.
-
The conclusion of contracts. If a contract concludes without dispute, each party broadcasts a signed message "The contract with SHA-1 hash H concludes without reparations." or possibly "The contract with SHA-1 hash H concludes with the following reparations: ..." Upon the broadcast of all signatures, every participant credits the account of each party by the amount of his maximum reparation, removes the contract account, then credits or debits the account of each party according to the reparation schedule if there is one.
-
The enforcement of contracts. If the parties to a contract cannot agree on an appropriate conclusion even with the help of the arbitrator, each party broadcasts a suggested reparation/fine schedule and any arguments or evidence in his favor. Each participant makes a determination as to the actual reparations and/or fines, and modifies his accounts accordingly.
In the second protocol, the accounts of who has how much money are kept by a subset of the participants (called servers from now on) instead of everyone. These servers are linked by a Usenet-style broadcast channel. The format of transaction messages broadcasted on this channel remain the same as in the first protocol, but the affected participants of each transaction should verify that the message has been received and successfully processed by a randomly selected subset of the servers.
Since the servers must be trusted to a degree, some mechanism is needed to keep them honest. Each server is required to deposit a certain amount of money in a special account to be used as potential fines or rewards for proof of misconduct. Also, each server must periodically publish and commit to its current money creation and money ownership databases. Each participant should verify that his own account balances are correct and that the sum of the account balances is not greater than the total amount of money created. This prevents the servers, even in total collusion, from permanently and costlessly expanding the money supply. New servers can also use the published databases to synchronize with existing servers.
The protocol proposed in this article allows untraceable pseudonymous entities to cooperate with each other more efficiently, by providing them with a medium of exchange and a method of enforcing contracts. The protocol can probably be made more efficient and secure, but I hope this is a step toward making crypto-anarchy a practical as well as theoretical possibility.
Appendix A: alternative b-money creation
One of the more problematic parts in the b-money protocol is money creation. This part of the protocol requires that all of the account keepers decide and agree on the cost of particular computations. Unfortunately because computing technology tends to advance rapidly and not always publicly, this information may be unavailable, inaccurate, or outdated, all of which would cause serious problems for the protocol.
So I propose an alternative money creation subprotocol, in which account keepers (everyone in the first protocol, or the servers in the second protocol) instead decide and agree on the amount of b-money to be created each period, with the cost of creating that money determined by an auction. Each money creation period is divided up into four phases, as follows:
-
Planning. The account keepers compute and negotiate with each other to determine an optimal increase in the money supply for the next period. Whether or not the account keepers can reach a consensus, they each broadcast their money creation quota and any macroeconomic calculations done to support the figures.
-
Bidding. Anyone who wants to create b-money broadcasts a bid in the form of <x, y=""> where x is the amount of b-money he wants to create, and y is an unsolved problem from a predetermined problem class. Each problem in this class should have a nominal cost (in MIPS-years say) which is publicly agreed on.
-
Computation. After seeing the bids, the ones who placed bids in the bidding phase may now solve the problems in their bids and broadcast the solutions.
-
Money creation. Each account keeper accepts the highest bids (among those who actually broadcasted solutions) in terms of nominal cost per unit of b-money created and credits the bidders' accounts accordingly.
Source:
http://www.weidai.com/bmoney.txt




(A message distributed on the Internet in the fall of 1993)
Introduction to BlackNet
Your name has come to our attention. We have reason to believe you may be interested in the products and services our new organization, BlackNet, has to offer.
BlackNet is in the business of buying, selling, trading, and otherwise dealing with *information* in all its many forms.
We buy and sell information using public key cryptosystems with essentially perfect security for our customers. Unless you tell us who you are (please don't!) or inadvertently reveal information which provides clues, we have no way of identifying you,nor you us.
Our location in physical space is unimportant. Our location in cyberspace is all that matters. Our primary address is the PGP key location:
"BlackNet<nowhere@cyberspace.nil>" and we can be contacted (preferably through a chain of anonymous remailers) by encrypting a message to our public key (contained below) and depositing this message in one of the several locations in cyberspace we monitor. Currently, we monitor the following locations: alt.extropians, alt.fan.david-sternlight, and the "Cypherpunks" mailing list.
BlackNet is nominally nondideological, but considers nation-states, export laws, patent laws, national security considerations and the like to be relics of the pre-cyberspace era. Export and patent laws are often used to explicity project national power and imperialist, colonialist state fascism. BlackNet believes it is solely the responsibility of a secret
holder to keep that secret--not the responsibilty of the State, or of us,or of anyone else who may come into possession of that secret. If a secret's worth having, it's worth protecting.
BlackNet is currently building its information inventory. We are interested in information in the following areas, though any other juicy stuff is always welcome. "If you think it's valuable, offer it to us first."
- trade secrets, processes, production methods (esp. in semiconductors)
- nanotechnology and related techniques (esp. the Merkle sleeve bearing)
- chemical manufacturing and rational drug design (esp. fullerines and protein folding)
- new product plans, from children's toys to cruise missiles (anything on "3DO"?)
- business intelligence, mergers, buyouts, rumors
BlackNet can make anonymous deposits to the bank account of your choice, where local banking laws permit, can mail cash directly (you assume the risk of theft or seizure), or can credit you in "CryptoCredits," the internal currency of BlackNet (which you then might use to buy _other_ information and have it encrypted to your special public key and posted in public place).
If you are interested, do NOT attempt to contact us directly (you'll be wasting your time), and do NOT post anything that contains your name, your e-mail address, etc. Rather, compose your message, encrypt it with the public key of BlackNet (included below), and use an anonymous remailer chain of one or more links to post this encrypted, anonymized message in one of the locations listed (more will be added later). Be sure to describe what you are selling, what value you think it has, your payment terms, and, of course, a special public key (NOT the one you use in your ordinary business, of course!) that we can use to get back in touch with you. Then watch the same public spaces for a reply.
(With these remailers, local PGP encryption within the remailers, the use of special public keys, and the public postings of the encrypted messages, a secure, two-way, untraceable, and fully anonymous channel has been opened between the customer and BlackNet. This is the key to BlackNet.)
A more complete tutorial on using BlackNet will soon appear, in plaintext form, in certain locations in cyberspace.
Join us in this revolutionary--and profitable--venture.
BlackNet<nowhere@cyberspace.nil>
Source:
https://groups.csail.mit.edu/mac/classes/
Original writings by Timothy C. May
Crypto Anarchy and Virtual Communities
Timothy C. May
535 Monterey Drive
Aptos, CA 95003 U.S.A.
tcmay@netcom.com
December, 1994
Source:
http://groups.csail.mit.edu
Extended Abstract
The combination of strong, unbreakable public key cryptography and virtual network communities in cyberspace will produce interesting and profound changes in the nature of economic and social systems. Crypto anarchy is the cyberspatial realization of anarcho-capitalism, transcending national boundaries and freeing individuals to make the economic arrangements they wish to make consensually.
Strong cryptography, exemplified by RSA (a public key algorithm) and PGP (Pretty Good Privacy), provides encryption that essentially cannot be broken with all the computing power in the universe. This ensures security and privacy. Public key cryptography is rightly considered to be a revolution.
Digital mixes, or anonymous remailers, use crypto to create untraceable e-mail, which has many uses. (Numerous anonymous remailers, in several countries, are now operating. Message traffic is growing exponentially.)
Digital pseudonyms, the creation of persistent network personas that cannot be forged by others and yet which are unlinkable to the "true names" of their owners, are finding major uses in ensuring free speech, in allowing controversial opinions to be aired, and in providing for economic transactions that cannot be blocked by local governments. The technology being deployed by the Cypherpunks and others, means their identities, nationalities, and even which continents they are on are untraceable -- unless they choose to reveal this information. This alters the conventional "relationship topology" of the world, allowing diverse interactions without external governmental regulation, taxation, or interference
Digital cash, untraceable and anonymous (like real cash), is also coming, though various technical and practical hurdles remain. "Swiss banks in cyberspace" will make economic transactions much more liquid and much less subject to local rules and regulations. Tax avoidance is likely to be a major attraction for many. An example of local interest to Monte Carlo might be the work underway to develop anonymous, untraceable systems for "cyberspace casinos." While not as attractive to many as elegant casinos, the popularity of "numbers games" and bookies in general suggests a opportunity to pursue.
Data havens and information markets are already springing up, using the methods described to make information retrievable anonymously and untraceably.
Governments see their powers eroded by these technologies, and are taking various well-known steps to try to limit the use of strong crypto by their subjects. The U.S. has several well-publicized efforts, including the Clipper chip, the Digital Telephony wiretap law, and proposals for "voluntary" escrow of cryptographic keys. Cypherpunks and others expect these efforts to be bypassed. Technology has let the genie out of the bottle. Crypto anarchy is liberating individuals from coercion by their physical neighbors--who cannot know who they are on the Net--and from governments. For libertarians, strong crypto provides the means by which government will be avoided.
The presentation will describe how several of these systems work, briefly, and will outline the likely implications of this combination of crypto anarchy and virtual cyberspace communities.
1 Introduction
This paper describes the combination of two major technologies:
- Strong Crypto: including encryption, digital signatures, digital cash, digital mixes (remailers), and related technologies.
- Cyberspatial Virtual Communities: including networks, anonymous communications, MUDs and MOOs, and "Multiverse"-type virtual realities.
These areas have generally remained separate, at least in published papers. Certainly the developers of cyberspace systems, such as MUDs, MOOs, and Habitat-like systems, appreciate the importance of cryptography for user authentication, overall security, and certainly for (eventual) digital purchase of services. But for the most part the combination of these two areas has been the province of the science fiction writer, notably writers such as Vernor Vinge, William Gibson, Bruce Sterling, and Orson Scott Card.
The "Cypherpunks" group, a loose, anarchic mailing list and group of hackers, was formed by several of us in 1992 as a group to make concrete some of the abstract ideas often presented at conferences. We've had some successes, and some failures. [1] The Cypherpunks group also appeared at a fortuitous time, as PGP was becoming popular, as Wired magazine appeared (they featured us on the cover of their second issue), and as the publicity (hype?) about the Information Superhighway and the World Wide Web reached a crescendo.
The site ftp.csua.berkeley.edu has a number of essays and files, including crypto files, in the directory pub/cypherpunks. I have also written/ compiled a very large 1.3 MB FAQ on these issues, the Cyphernomicon, available at various sites, including my ftp directory, ftp.netcom.com, in the directory pub/tc/tcmay.
The Cypherpunks group is also a pretty good example of a "virtual community." Scattered around the world, communicating electronically in matters of minutes, and seeming oblivious to local laws, the Cypherpunks are indeed a community, and a virtual one. Many members use pseudonyms, and use anonymous remailers to communicate with the list. The list itself thus behaves as a "message pool," a place where information of all sort may be anonymous deposited--and anonymous received (since everyone sees the entire list, like a newspaper, the intended recipient is anonymized).
Legal Caveat: Consult your local laws before applying any of the methods described here. In some jurisdictions, it may be illegal to even read papers like this (seriously). In particular, I generally won't be giving ftp site addresses for copies of PGP, remailer access, digital cash systems, etc. These are well-covered in more current forums, e.g., sci.crypt or talk.politics.crypto, and there are some unresolved issues about whether giving the address of such sites constitutes (or "aids and abets") violation of various export and munitions laws (crypto is considered a munition in the U.S. and probably elsewhere....some nations consider a laser printer to be a munitions item!).
2 Modern Cryptography
The past two decades have produced a revolution in cryptography (crypto, for short) the science of the making of ciphers and codes. Beyond just simple ciphers, useful mainly for keeping communications secret, modern crypto includes diverse tools for authentication of messages, for digital timestamping of documents, for hiding messages in other documents (steganography), and even for schemes for digital cash.
Public key cryptography, the creation of Diffie and Hellman, has dramatically altered the role of crypto. Coming at the same time as the wholesale conversion to computer networks and worldwide communications, it has been a key element of security, confidence, and success. The role of crypto will only become more important over the coming decades.
Pretty Good Privacy, PGP, is a popular version of the algorithm developed by Rivest, Shamir, and Adleman, known of course as RSA. The RSA algorithm was given a patent in the U.S., though not in any European countries, and is licensed commercially. [2]
These tools are described in detail in various texts and Conference proceedings, and are not the subject of this paper. [3] The focus here is on the implications of strong crypto for cyberspace, especially on virtual communities.
Mention should be made of the role of David Chaum in defining the key concepts here. In several seminal papers (for example, [4] [5]), Chaum introduced the ideas of using public key cryptography methods for anonymous, untraceable electronic mail, for digital money systems in which spender identity is not revealed, and in schemes related to these. (I make no claims of course that Chaum agrees with my conclusions about the political and socioeconomic implications of these results.)
3 Virtual Communities
Notes: cyberspace, Habitat, VR, Vinge, etc. Crypto holds up the "walls" of these cyberspatial realities. Access control, access rights, modification privileges.
Virtual communities are the networks of individuals or groups which are not necessarily closely-connected geographically. The "virtual" is meant to imply a non-physical linking, but should not be taken to mean that these are any less community-like than are conventional physical communities.
Examples include churches, service organizations, clubs, criminal gangs, cartels, fan groups, etc. The Catholic Church and the Boy Scouts are both examples of virtual communities which span the globe, transcend national borders, and create a sense of allegiance, of belonging, and a sense of "community." Likewise, the Mafia is a virtual community (with its enforcement mechanisms, its own extra-legal rules, etc.) Lots of other examples: Masons, Triads, Red Cross, Interpol, Islam, Judaism, Mormons, Sindero Luminoso, the IRA, drug cartels, terrorist groups, Aryan Nation, Greenpeace, the Animal Liberation Front, and so on. There are undoubtedly many more such virtual communities than there are nation-states, and the ties that bind them are for the most part much stronger than are the chauvinist nationalism emotions. Any group in which the common interests of the group, be it a shared ideology or a particular interest, are enough to create a cohesive community.
Corporations are another prime example of a virtual community, having scattered sites, private communication channels (generally inaccessible to the outside world, including the authorities), and their own goals and methods. In fact, many "cyberpunk" (not cypherpunk) fiction authors make a mistake, I think, in assuming the future world will be dominated by transnational megacorporate "states." In fact, corporations are just one example--of many--of such virtual communities which will be effectively on a par with nation-states. (Note especially that any laws designed to limit use of crypto cause immediate and profound problems for corporations-countries like France and the Philippines, which have attempted to limit the use of crypto, have mostly been ignored by corporations. Any attempts to outlaw crypto will produce a surge of sudden "incorporations," thus gaining for the new corporate members the aegis of corporate privacy.)
In an academic setting, "invisible colleges" are the communities of researchers.
These virtual communities typically are "opaque" to outsiders. Attempts to gain access to the internals of these communities are rarely successful. Law enforcement and intelligence agencies (such as the NSA in the U.S., Chobetsu in Japan, SDECE in France, and so on, in every country) may infiltrate such groups and use electronic surveillance (ELINT) to monitor these virtual communities. Not surprisingly, these communities are early adopters of encryption technology, ranging from scrambled cellphones to full-blown PGP encryption. [8]
The use of encryption by "evil" groups, such as child pornographers, terrorists, abortionists, abortion protestors, etc., is cited by those who wish to limit civilian access to crypto tools. We call these the "Four Horseman of the Infocalypse," as they are so often cited as the reason why ordinary citizen-units of the nation-state are not to have access to crypto.
This is clearly a dangerous argument to make, for various good reasons. The basic right of free speech is the right to speak in a language one's neighbors or governing leaders may not find comprehensible: encrypted speech. There's not enough space here to go into the many good arguments against a limit on access to privacy, communications tools, and crypto.
The advent of full-featured communications systems for computer-mediated virtual communities will have even more profound implications. MUDs and MOOs (multi-user domains, etc.) and 3D virtual realities are one avenue, and text-centric Net communications are another. (Someday, soon, they'll merge, as described in Vernor Vinge's prophetic 1980 novella, True Names.)
4 Observability and Surveillance
An interesting way to view issues of network visibility is in terms of the "transparency" of nodes and links between nodes. Transparent means visible to outsiders, perhaps those in law enforcement or the intelligence community. Opaque mean not transparent, not visible. A postcard is transparent, a sealed letter is opaque. PGP inventor Phil Zimmermann has likened the requirement for transparency to being ordered to use postcards for all correspondence, with encryption the equivalent of an opaque envelope (envelopes can be opened, of course, and long have been).
Transparent links and nodes are the norm in a police state, such as the U.S.S.R., Iraq, China, and so forth. Communications channels are tapped, and private use of computers is restricted. (This is becoming increasingly hard to do, even for police states; many cite the spread of communications options as a proximate cause of the collapse of communism in recent years.)
There are interesting "chemistries" or "algebras" of transparent vs. opaque links and nodes. What happens if links must be transparent, but nodes are allowed to be opaque? (The answer: the result is as if opaque links and nodes were allowed, i.e., full implications of strong crypto. Hence, any attempt to ban communications crypto while still allowing private CPUs to exist....)
If Alice and Bob are free to communicate, and to choose routing paths, then Alice can use "crypto arbitrage" (a variation on the term, "regulatory arbitrage," the term Eric Hughes uses to capture this idea of moving transactions to other jurisdictions) to communicate with sites--perhaps in other countries--that will perform as she wishes. This can mean remailing, mixing, etc. As an example, Canadian citizens who are told they cannot access information on the Homolka-Teale murder case (a controversial case in which the judge has ordered the media in Canada, and entering Canada, not to discuss the gory details) nevertheless have a vast array of options, including using telnet, gopher, ftp, the Web, etc., to access sites in many other countries--or even in no country in particular.
Most of the consequences described here arise from this chemistry of links and nodes: unless nearly all node and links are forced to be transparent, including links to other nations and the nodes in those nations, then the result is that private communication can still occur. Crypto anarchy results.
5 Crypto Anarchy
"The Net is an anarchy." This truism is the core of crypto anarchy. No central control, no ruler, no leader (except by example, reputation), no "laws." No single nation controls the Net, no administrative body sets policy. The Ayatollah in Iran is as powerless to stop a newsgroup--alt.wanted.moslem.women or alt.wanted.moslem.gay come to mind-he doesn't like as the President of France is as powerless to stop, say, the abuse of French in soc.culture.french. Likewise, the CIA can't stop newsgroups, or sites, or Web pages, which give away their secrets. At least not in terms of the Net itself...what non-Net steps might be taken is left as an exercise for the paranoid and the cautious.
This essential anarchy is much more common than many think. Anarchy--the absence of a ruler telling one what to do--is common in many walks of life: choice of books to read, movies to see, friends to socialize with, etc. Anarchy does not mean complete freedom--one can, after all, only read the books which someone has written and had published--but it does mean freedom from external coercion. Anarchy as a concept, though, has been tainted by other associations.
First, the "anarchy" here is not the anarchy of popular conception: lawlessness, disorder, chaos, and "anarchy." Nor is it the bomb-throwing anarchy of the 19th century "black" anarchists, usually associated with Russia and labor movements. Nor is it the "black flag" anarchy of anarcho-syndicalism and writers such as Proudhon. Rather, the anarchy being spoken of here is the anarchy of "absence of government" (literally, "an arch," without a chief or head).
This is the same sense of anarchy used in "anarchocapitalism," the libertarian free market ideology which promotes voluntary, uncoerced economic transactions. [6] I devised the term crypto anarchy as a pun on crypto, meaning "hidden," on the use of "crypto" in combination with political views (as in Gore Vidal's famous charge to William F. Buckley: "You crypto fascist!"), and of course because the technology of crypto makes this form of anarchy possible. The first presentation of this was in a 1988 "Manifesto," whimsically patterned after another famous manifesto. [7] Perhaps a more popularly understandable term, such as "cyber liberty," might have some advantages, but crypto anarchy has its own charm, I think.
And anarchy in this sense does not mean local hierarchies don't exist, nor does it mean that no rulers exist. Groups outside the direct control of local governmental authorities may still have leaders, rulers, club presidents, elected bodies, etc. Many will not, though.
Politically, virtual communities outside the scope of local governmental control may present problems of law enforcement and tax collection. (Some of us like this aspect.) Avoidance of coerced transactions can mean avoidance of taxes, avoidance of laws saying who one can sell to and who one can't, and so forth. It is likely that many will be unhappy that some are using cryptography to avoid laws designed to control behavior.
National borders are becoming more transparent than ever to data. A flood of bits crosses the borders of most developed countries--phone lines, cables, fibers, satellite up/downlinks, and millions of diskettes, tapes, CDs, etc. Stopping data at the borders is less than hopeless.
Finally, the ability to move data around the world at will, the ability to communicate to remote sites at will, means that a kind of "regulatory arbitrage" can be used to avoid legal roadblocks. For example, remailing into the U.S. from a site in the Netherlands...whose laws apply? (If one thinks that U.S. laws should apply to sites in the Netherlands, does Iraqi law apply in the U.S.? And so on.)
This regulatory arbitrage is also useful for avoiding the welter of laws and regulations which operations in one country may face, including the "deep pockets" lawsuits so many in the U.S. face. Moving operations on the Net outside a litigious jurisdiction is one step to reduce this business liability. Like Swiss banks, but different.
6 True Names and Anonymous Systems
Something needs to be said about the role of anonymity and digital pseudonyms. This is a topic for an essay unto itself, of course.
Are true names really needed? Why are they asked for? Does the nation-state have any valid reason to demand they be used?
People want to know who they are dealing with, for psychological/evolutionary reasons and to better ensure traceability should they need to locate a person to enforce the terms of a transaction. The purely anonymous person is perhaps justifiably viewed with suspicion.
And yet pseudonyms are successful in many cases. And we rarely know whether someone who presents himself by some name is "actually" that person. Authors, artists, performers, etc., often use pseudonyms. What matters is persistence, and nonforgeability. Crypto provides this.
On the Cypherpunks list, well-respected digital pseudonyms have appeared and are thought of no less highly than their "real" colleagues are.
The whole area of digitally-authenticated reputations, and the "reputation capital" that accumulates or is affected by the opinions of others, is an area that combines economics, game theory, psychology, and expectations. A lot more study is needed.
It is unclear if governments will move to a system of demanding "Information Highway Driver's Licenses," figuratively speaking, or how systems like this could ever be enforced. (The chemistry of opaque nodes and links, again.)
7 Examples and Uses
It surprises many people that some of these uses are already being intensively explored. Anonymous remailers are used by tens of thousands of persons-and perhaps abused. [13] And of course encryption, via RSA, PGP, etc., is very common in some communities. (Hackers, Net users, freedom fighters, white separatists, etc....I make no moral judgments here about those using these methods).
Remailers are a good example to look at in more detail. There are two current main flavors of remailers:
- "Cypherpunk"-style remailers, which process text messages to redirect mail to another sites, using a command syntax that allows arbitrary nesting of remailing (as many sites as one wishes), with PGP encryption at each level of nesting.
- "Julf"-style remailer(s), based on the original work of Karl Kleinpaste and operated/maintained by Julf Helsingius, in Finland. No encryption, and only one such site at present. (This system has been used extensively for messages posted to the Usenet, and is basically successful. The model is based on operator trustworthiness, and his location in Finland, beyond the reach of court orders and subpoenas from most countries.)
The Cypherpunks remailers currently number about 20, with more being added every month. There is no reason not to expect hundreds of such remailers in a few years.
One experimental "information market" is BlackNet, a system which appeared in 1993 and which allows fully-anonymous, two-way exchanges of information of all sorts. There are reports that U.S. authorities have investigated this because of its presence on networks at Defense Department research labs. Not much they can do about it, of course, and more such entities are expected.
(The implications for espionage are profound, and largely unstoppable. Anyone with a home computer and access to the Net or Web, in various forms, can use these methods to communicate securely, anonymously or pseudonymously, and with little fear of detection. "Digital dead drops" can be used to post information obtained, far more securely than the old physical dead drops...no more messages left in Coke cans at the bases of trees on remote roads.)
Whistleblowing is another growing use of anonymous remailers, with folks fearing retaliation using remailers to publicly post information. (Of course, there's a fine line between whistleblowing, revenge, and espionage.)
Data havens, for the storage and marketing of controversial information is another area of likely future growth. Nearly any kind of information, medical, religious, chemical, etc., is illegal or proscribed in one or more countries, so those seeking this illegal information will turn to anonymous messaging systems to access--and perhaps purchase, with anonymous digital cash--this information. This might include credit data bases, deadbeat renter files, organ bank markets, etc. (These are all things which have various restrictions on them in the U.S., for example....one cannot compile credit data bases, or lists of deadbeat renters, without meeting various restrictions. A good reason to move them into cyberspace, or at least outside the U.S., and then sell access through remailers.)
Matching buyers and sellers of organs is another such market. A huge demand (life and death), but various laws tightly controlling such markets.
Digital cash efforts. A lot has been written about digital cash. [14] [15] David Chaum's company, DigiCash, has the most interesting technology, and has recently begun market testing. Stefan Brands may or may not have a competing system which gets around some of Chaum's patents. (The attitude crypto anarchists might take about patents is another topic for discussion. Suffice it to say that patents and other intellectual property issues continue to have relevance in the practical world, despite erosion by technological trends.)
Credit card-based systems, such as the First Virtual system, are not exactly digital cash, in the Chaumian sense of blinded notes, but offer some advantages the market may find useful until more advanced systems are available.
I expect to see many more such experiments over the next several years, and some of them will likely be market successes.
8 Commerce and Colonization of Cyberspace
How will these ideas affect the development of cyberspace?
"You can't eat cyberspace" is a criticism often levelled at argument about the role of cyberspace in everyday life. The argument made is that money and resources "accumulated" in some future (or near-future) cyberspatial system will not be able to be "laundered" into the real world. Even such a prescient thinker as Neal Stephenson, in Snow Crash, had his protagonist a vastly wealthy man in "The Multiverse," but a near-pauper in the physical world.
This is implausible for several reasons. First, we routinely see transfers of wealth from the abstract world of stock tips, arcane consulting knowledge, etc., to the real world. "Consulting" is the operative word. Second, a variety of means of laundering money, via phony invoices, uncollected loans, art objects, etc., are well-known to those who launder money...these methods, and more advanced ones to come, are likely to be used by those who wish their cyberspace profits moved into the real world.
(Doing this anonymously, untraceably, is another complication. There may be methods of doing this--proposals have looked pretty solid, but more work is needed.)
The World Wide Web is growing at an explosive pace. Combined with cryptographically-protected communication and digital cash of some form (and there are several being tried), this should produce the long-awaited colonization of cyberspace.
Most Net and Web users already pay little attention to the putative laws of their local regions or nations, apparently seeing themselves more as members of various virtual communities than as members of locally-governed entities. This trend is accelerating.
Most importantly, information can be bought and sold (anonymously, too) and then used in the real world. There is no reason to expect that this won't be a major reason to move into cyberspace.
9 Implications
I've touched on the implications in several places. Many thoughtful people are worried about some of the possibilities made apparent by strong crypto and anonymous communication systems. Some are proposing restrictions on access to crypto tools. The recent debate in the U.S. over "Clipper" and other key escrow systems shows the strength of emotions on this issue.
Abhorrent markets may arise. For example, anonymous systems and untraceable digital cash have some obvious implications for the arranging of contract killings and such. (The greatest risk in arranging such hits is that physical meetings expose the buyers and sellers of such services to stings. Crypto anarchy lessens, or even eliminates, this risk, thus lowering transaction costs. The risks to the actual triggermen are not lessened, but this is a risk the buyers need not worry about. Think of anonymous escrow services which hold the digital money until the deed is done. Lots of issues here. It is unfortunate that this area is so little-discussed....people seem to have an aversion for exploring the logical consequences in such areas.)
The implications for corporate and national espionage have already been touched upon. Combined with liquid markets in information, this may make secrets much harder to keep. ((Imagine a "Digital Jane's," after the military weapons handbooks, anonymously compiled and sold for digital money, beyond the reach of various governments which don't want their secrets told.)
New money-laundering approaches are of course another area to explore.
Something that is inevitable is the increased role of individuals, leading to a new kind of elitism. Those who are comfortable with the tools described here can avoid the restrictions and taxes that others cannot. If local laws can be bypassed technologically, the implications are pretty clear.
The implications for personal liberty are of course profound. No longer can nation-states tell their citizen-units what they can have access to, not if these citizens can access the cyberspace world through anonymous systems.
10 How Likely?
I am making no bold predictions that these changes will sweep the world anytime soon. Most people are ignorant of these methods, and the methods themselves are still under development. A wholesale conversion to "living in cyberspace" is just not in the cards, at least not in the next few decades.
But to an increasingly large group, the Net is reality. It is where friends are made, where business is negotiated, where intellectual stimulation is found. And many of these people are using crypto anarchy tools. Anonymous remailers, message pools, information markets. Consulting via pseudonyms has begun to appear, and should grow. (As usual, the lack of a robust digital cash system is slowing things down.
Can crypto anarchy be stopped? Although the future evolution in unclear, as the future almost always is, it seems unlikely that present trends can be reversed:
- Dramatic increases in bandwidth and local, privately-owned computer power.
- Exponential increase in number of Net users.
- Explosion in "degrees of freedom" in personal choices, tastes, wishes, goals.
- Inability of central governments to control economies, cultural trends, etc. [9]
The Net is integrally tied to economic transactions, and no country can afford to "disconnect" itself from it. (The U.S.S.R. couldn't do it, and they were light-years behind the U.S., European, and Asian countries. And in a few more years, no hope of limiting these tools at all, something the U.S. F.B.I. has acknowledged. [11]
Technological Inevitability: These tools are already in widespread use, and only draconian steps to limit access to computers and communications channels could significantly impact further use. (Scenarios for restrictions on private use of crypto.)
As John Gilmore has noted, "the Net tends to interpret censorship as damage, and routes around it." This applies as well to attempts to legislate behavior on the Net. (The utter impossibility of regulating the worldwide Net, with entry points in more than a hundred nations, with millions of machines, is not yet fully recognized by most national governments. They still speak in terms of "controlling" the Net, when in fact the laws of one nation generally have little use in other countries.)
Digital money in its various forms is probably the weakest link at this point. Most of the other pieces are operational, at least in basic forms, but digital cash is (understandably) harder to deploy. Hobbyist or "toy" experiments have been cumbersome, and the "toy" nature is painfully obvious. It is not easy to use digital cash systems at this time ("To use Magic Money, first create a client..."), especially as compared to the easily understood alternatives. [12] People are understandably reluctant to entrust actual money to such systems. And it's not yet clear what can be bought with digital cash (a chicken or egg dilemma, likely to be resolved in the next several years).
And digital cash, digital banks, etc., are a likely target for legislative moves to limit the deployment of crypto anarchy and digital economies. Whether through banking regulation or tax laws, it is not likely that digital money will be deployed easily. "Kids, don't try this at home!" Some of the current schemes may also incorporate methods for reporting transactions to the tax authorities, and may include "software key escrow" features which make transactions fully or partly visible to authorities.
11 Conclusions
Strong crypto provides new levels of personal privacy, all the more important in an era of increased surveillance, monitoring, and the temptation to demand proofs of identity and permission slips. Some of the "credentials without identity" work of Chaum and others may lessen this move toward a surveillance society.
The implications are, as I see it, that the power of nation-states will be lessened, tax collection policies will have to be changed, and economic interactions will be based more on personal calculations of value than on societal mandates.
Is this a Good Thing? Mostly yes. Crypto anarchy has some messy aspects, of this there can be little doubt. From relatively unimportant things like price-fixing and insider trading to more serious things like economic espionage, the undermining of corporate knowledge ownership, to extremely dark things like anonymous markets for killings.
But let's not forget that nation-states have, under the guise of protecting us from others, killed more than 100 million people in this century alone. Mao, Stalin, Hitler, and Pol Pot, just to name the most extreme examples. It is hard to imagine any level of digital contract killings ever coming close to nationstate barbarism. (But I agree that this is something we cannot accurately speak about; I don't think we have much of a choice in embracing crypto anarchy or not, so I choose to focus on the bright side.)
It is hard to argue that the risks of anonymous markets and tax evasion are justification for worldwide suppression of communications and encryption tools. People have always killed each other, and governments have not stopped this (arguably, they make the problem much worse, as the wars of this century have shown).
Also, there are various steps that can be taken to lessen the risks of crypto anarchy impinging on personal safety. [10]
Strong crypto provides a technological means of ensuring the practical freedom to read and write what one wishes to. (Albeit perhaps not in one's true name, as the nation-state-democracy will likely still try to control behavior through majority votes on what can be said, not said, read, not read, etc.) And of course if speech is free, so are many classes of economic interaction that are essentially tied to free speech.
A phase change is coming. Virtual communities are in their ascendancy, displacing conventional notions of nationhood. Geographic proximity is no longer as important as it once was.
A lot of work remains. Technical cryptography still hasn't solved all problems, the role of reputations (both positive and negative) needs further study, and the practical issues surrounding many of these areas have barely been explored.
We will be the colonizers of cyberspace.
12 Acknowledgments
My thanks to my colleagues in the Cypherpunks group, all 700 of them, past or present. Well over 100 megabytes of list traffic has passed through he Cypherpunks mailing list, so there have been a lot of stimulating ideas. But especially my appreciation goes to Eric Hughes, Sandy Sandfort, Duncan Frissell, Hal Finney, Perry Metzger, Nick Szabo, John Gilmore, Whit Diffie, Carl Ellison, Bill Stewart, and Harry Bartholomew. Thanks as well to Robin Hanson, Ted Kaehler, Keith Henson, Chip Morningstar, Eric Dean Tribble, Mark Miller, Bob Fleming, Cherie Kushner, Michael Korns, George Gottlieb, Jim Bennett, Dave Ross, Gayle Pergamit, and--especially--the late Phil Salin. Finally, thanks for valuable discussions, sometimes brief, sometimes long, with Vernor Vinge, David Friedman, Rudy Rucker, David Chaum, Kevin Kelly, and Steven Levy.
13 References and Notes
1 The Cypherpunks group was mainly formed by Eric Hughes, Tim May, and John Gilmore. It began both physical meetings, in the Bay Area and elsewhere, and virtual meetings on an unmoderated mailing list. The name was provided by Judith Milhon, as a play on the "cyberpunk" genre and the British spelling of cipher. The mailing list can be subscribed to by sending the single message subscribe cypherpunks in the body of a message to majordomo@toad.com. Expect at least 50 messages a day. About 600 subscribers in many countries are presently on the list. Some are pseudonyms.
2 RSA Data Security Inc., Redwood Shores, California, is the license administrator. Contact them for details.
3 Many crypto texts exist. A good introduction is Bruce Schneier's Applied Cryptography, John Wiley and Sons, 1994. This text includes pointers to many other sources. The "Crypto" Proceedings (Advances in Cryptology, Springer-Verlag, annually) are essential references. The annual Crypto conference in Santa Barbara, and the Eurocrypt and Auscrypt conferences, are where most crypto results are presented.
4 David Chaum, "Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms," Comm. ACM 24, 2, February 1981, pp. 84-88. Cypherpunks-style remailers are a form of Chaum's "digital mixes," albeit far from ideal.
5 David Chaum, "Security without Identification: Transaction Systems to make Big Brother Obsolete," Comm. ACM 28, 10, October 1985. This is an early paper on digital cash...be sure to consult more recent papers.
6 David Friedman, The Machinery of Freedom, 2nd edition. A leading theoretician of anarcho-capitalism. (Hayek was another.)
7 Tim May, The Crypto Anarchist Manifesto, July 1988, distributed on the Usenet and on various mailing lists.
8 The political opposition in Myan Mar--formerly Burma--is using Pretty Good Privacy running on DOS laptops in the jungles for communications amongst the rebels, according to Phil Zimmermann, author of PGP. This life-and-death usage underscores the role of crypto.
9 See Kevin Kelly's Out of Control, 1994, for a discussion of how central control is failing, and how the modern paradigm is one of market mechanisms, personal choice, and technological empowerment.
10 Robin Hanson and David Friedman have written extensively about scenarios for dealing with the threats of extortionists, would-be assassins, etc. I am hoping some of their work gets published someday. (Much of the discussion was in 1992-3, on the "Extropians" mailing list.)
11 During the "Digital Telephony Bill" debate, an FBI official said that failure to mandate wiretap capabilities within the next 18 months would make it all moot, as the cost would rise beyond any reasonable budget (currently $500 million for retrofit costs).
12 "Magic Money" was an experimental implementation of Chaum's digital cash system. It was coded by "Pr0duct Cypher," a pseudonymous member of the Cypherpunks list--none of us knows his real identity, as he used remailers to communicate with the list, and digitally signed his posts. Many of us found it too difficult to use, which is more a measure of the deep issues involved in using digital analogs (no pun intended) to real, physical money.
13 Abuse, according to some views, of remailers is already occurring. A Cypherpunks-type remailer was used to post a proprietary hash function of RSA Data Security, Inc. to the Usenet. (Let me hasten to add that it was not a remailer I operate, or have control over, etc.)
14 article on digital cash, The Economist, 26 November 1994. pp. 21-23.
15 article on digital cash, Steven Levy, Wired. December 1994.
Source:
http://groups.csail.mit.edu
From: tcmay@netcom.com (Timothy C. May)
Subject: The Crypto Anarchist Manifesto
Date: Sun, 22 Nov 92 12:11:24 PST
Cypherpunks of the World,
Several of you at the "physical Cypherpunks" gathering yesterday in Silicon Valley requested that more of the material passed out in meetings be available electronically to the entire readership of the Cypherpunks list, spooks, eavesdroppers, and all. <Gulp>
Here's the "Crypto Anarchist Manifesto" I read at the September 1992 founding meeting. It dates back to mid-1988 and was distributed to some like-minded techno-anarchists at the "Crypto '88" conference and then again at the "Hackers Conference" that year. I later gave talks at Hackers on this in 1989 and 1990.
There are a few things I'd change, but for historical reasons I'll just leave it as is. Some of the terms may be unfamiliar to you...I hope the Crypto Glossary I just distributed will help.
(This should explain all those cryptic terms in my .signature!)
--Tim May
...................................................
The Crypto Anarchist Manifesto
Timothy C. May <tcmay@netcom.com>
A specter is haunting the modern world, the specter of crypto anarchy.
Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re- routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation.
The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies.
The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy.
Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property.
Arise, you have nothing to lose but your barbed wire fences!
--
..........................................................................
Timothy C. May | Crypto Anarchy: encryption, digital money,
tcmay@netcom.com | anonymous networks, digital pseudonyms, zero
408-688-5409 | knowledge, reputations, information markets,
W.A.S.T.E.: Aptos, CA | black markets, collapse of governments.
Higher Power: 2^756839 | PGP Public Key: by arrangement.
Source:
https://www.activism.net/cypherpunk/crypto-anarchy.html

Appendix
The BlackNet Experiment
Tim May, 1997
A few years ago I devised a working information market, using PGP for secure communication and digital signatures, chained anonymous remailers for untraceability, and message pools (e.g., alt.anonymous.messages on Usenet) for making contact and sending later messages. My intention was to directly demonstrate the feasibility of such markets, and to explore some of the nuances of such markets. (At no point was BlackNet actually used for espionage, though I did get a few strange offers, including an offer to sell me information on how the CIA was targetting the diplomats of certain African nations in Washington.)
BlackNet allowed fully-anonymous, two-way exchanges of information of all sorts. The basic idea was to use a "message pool," a publicly readable place for messages. By using chains of remailers, messages could be untraceably and anonymously deposited in such pools, and then read anonymously by others (because the message pool was broadcast widely, a la Usenet). By including public keys for later communications, two-way communication could be established, all within the message pool. What was missing at the time of this experiment was some form of untraceable payment, i.e., digital cash.
As Paul Leyland so succinctly described the experiment:
"Tim May showed how mutually anonymous secure information trading could be implemented with a public forum such as usenet and with public key cryptography. Each information purchaser wishing to take part posts a sales pitch and a public key to Usenet. Information to be traded would then have a public key appended so that a reply can be posted and the whole encrypted in the public key of the other party. For anonymity, the keys should contain no information that links it to an identifiable person. May posted a 1024-bit PGP key supposedly belonging to "Blacknet". As May's purpose was only educational, he soon admitted authorship."
(I should add that copies of the BlackNet message circulated widely and even appeared at some national laboratories doing sensitive work. Oak Ridge issued an advisory warning employees to report any contacts with BlackNet!)
Source:
Untraceable Digital Cash, Information Markets, and BlackNet ("Governmental and Social Implications of Digital Money" panel at CFP '97)
Tim May
Corralitos, CA
tcmay@got.net
1996-09-17 - Re: Risk v. Charity (was: RE: Workers Paradise. /Political rant
Header Data
From: craigw@dg.ce.com.au
To: Black Unicorn <unicorn@schloss.li>
Message Hash: dfc75b84234ea728c6c34cb022dde758d44d5f9fb266d9a00092f593a9c93c6b
Message ID: <199609170703.RAA21552@mac.ce.com.au>
Reply To: N/A
UTC Datetime: 1996-09-17 11:38:06 UTC
Raw Date: Tue, 17 Sep 1996 19:38:06 +0800
Raw message
From: craigw@dg.ce.com.au
Date: Tue, 17 Sep 1996 19:38:06 +0800
To: Black Unicorn <unicorn@schloss.li>
Subject: Re: Risk v. Charity (was: RE: Workers Paradise. /Political rant
Message-ID: <199609170703.RAA21552@mac.ce.com.au>
MIME-Version: 1.0
Content-Type: text/plain
Personally, I paid my way through uni...full fees. I took out a loan
when I developed cancer to pay for it (as the health insurance was
not finalised for aproval - so they got out of paying). The few
months I was unemployed after I left the military because of a
confict of interests I earned money by doing whatever I could get
(even though I am an engineer I have worked in a petrol station). So
why and for what reason sould I have to pay several 10's of thousands
each year to support others. I have never taken help from the
govenment, I do not feel I should have to pay as well.
And what am I paying for...to protect the status quo. I believe that
there is more than enough help for ppl available. They just need to
get off their butts and work.
> > tcmay@got.net (Timothy C. May) wrote:
> > >"Saving for a rainy day," whether saving, investing, getting an education
> > (while others are out partying), preparing, etc., all takes effort and
> > commitment. If those who save and prepare are then told they have to pay
> > high taxes to support those who partied....well, the predictable effect
> > [...] is _more_ people in agony. When you tell people that a compassionate
> > society will meet their basic needs, a predictable fraction of them will choose
> > not to work hard and prepare themselves.
> >
> > Two questions, two observations:
> > Do you have health insurance?
> > Do you have life insurance?
>
> Yes, so?
> Yes, so?
Myself also yes,yes
> > I have commented on your line of reasoning before and and it still
> > seems to me that an important part of the discussion is missed.
> > Specifically, that anyone can "save for a rainy day" and still not be
> > able to provide for events that can always happen: Heart attack, stroke,
> > car accident, pinched nerve that leaves you in excruciating pain and
> > unable to work for several years.
>
> Understand what it is you are saying.
>
,'~``. \|/ ,'``~.
(-o=o-) (@ @) ,(-o=o-),
+--.oooO--(_)--Ooo-----oOO-(_)-OOo-------oooO--(_)--Oooo.------+
| |
| Soon, we may all be staring at our computers, wondering |
| whether they're staring back. |
| |
| [Network Admin For WPA Business Products. aka doshai >;-) ] |
| .oooO http://pip.com.au/~doshai/ Oooo. |
| ( ) Oooo. .oooO ( ) |
+-----\ (----( )-------oooO-Oooo--------( )--- ) /---------+
\_) ) / \ ( (_/
(_/ \_)
Key fingerprint = 2D F4 54 BB B4 EA F1 E7 B6 DE 48 92 FC 8D FF 49
Send a message with the subject "send pgp-key" for a copy of my key.
(if I want to give it to you)
Thread
Sources:
https://github.com/cryptoanarchywiki/mailing-list-archivehttp://cypherpunks.venona.com/date/1996/09/msg01451.html
From: pcl@sable.ox.ac.uk (Paul Leyland)
Newsgroups: alt.security.pgp,sci.crypt,alt.privacy
Subject: The BlackNet 384-bit PGP key has been BROKEN
Date: 26 Jun 1995 10:09:15 GMT
Organization: Oxford University, England
NNTP-Posting-Host: sable.ox.ac.uk
-----BEGIN PGP SIGNED MESSAGE-----
The BlackNet 384-bit PGP key has been BROKEN
We announce the first known hostile attack on a PGP public key.
In 1993, Tim May created BlackNet as a proof-of-concept implementation of an information trading business with cryptographically protected anonymity of the traders. He created a 1024-bit key, and invited mpotential traders to encrypt their sales pitch and a public key for a reply with the BlackNet key, posting the result in one or more Usenet newsgroups. BlackNet would then reply in the same manner. The original proposal went only to a few people and May acknowledged his authorship shortly afterwards, when his pedagogical point had been made. It was soon posted to the Cypherpunks list, and from there to Usenet. Six months afterwards in February 1994, a 384-bit key was created in the BlackNet name, and the BlackNet message was spammed to hundreds of newsgroups by the new key owner, L. Detweiler.
At least one message was posted encrypted in the 384-bit key. The encryptor, either by design or by unwitting use of PGP's encrypttoself option, also encrypted the message to his own key, exposing his identity to anyone who cared to look him up on the key servers and use finger.
Factoring 384-bit integers is not too difficult these days. We wantedto see whether it could be done surreptitiously. Jim Gillogly picked the 384-bit BlackNet key as a suitable target, partly because of its apparent interest and partly because he had saved a copy of the reply. Paul Leyland took the key to pieces. The public exponent was found to be 17 and the public modulus:
3193508200533105601431099148202479609827976414818808019973596061739243\
9454375249389462927646908605384634672078311787
READ ON
Source:
https://bico.media/

JavaScript is turned off.
Please enable JavaScript to view this site properly.